
ZeroTrusted.ai is the leading provider of Zero Trust Security products that leverage innovative technologies and machine learning to protect your network and systems. Our custom solutions are designed to meet key compliance metrics and achieve true Zero Trust Security, giving you peace of mind knowing your infrastructure is fully protected.

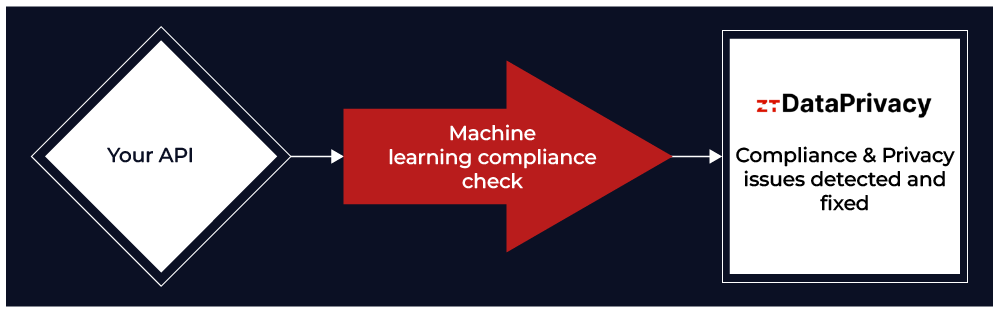
Data privacy is a critical concern, and traditional solutions like TLS/SSL are often insufficient in preventing potential eavesdropping from intermediate servers, especially when transmitting sensitive data via API.
Unlike other products in the market, ZeroTrusted.ai is engineered to fill this gap, offering a robust solution specifically designed to meet the stringent demands of zero-trust compliance.
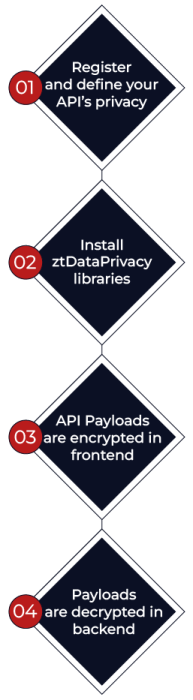

In the ztDataPrivacy portal, specify the OpenAPI doc URI to the API whose payload you want to protect, and enable encryption on as many API properties that you want to secure.
Add ztDataPrivacy libraries to your front-end application (i.e. Angular, React, etc) and your back-end application (i.e. .Net core, Node.js, etc).
Once libraries are installed, API payloads will be encrypted based on the configuration rules provided in Step 1.
Subsequently, in the back-end, API payloads will be decrypted or saved to the database in an encrypted state depending on the configurations.

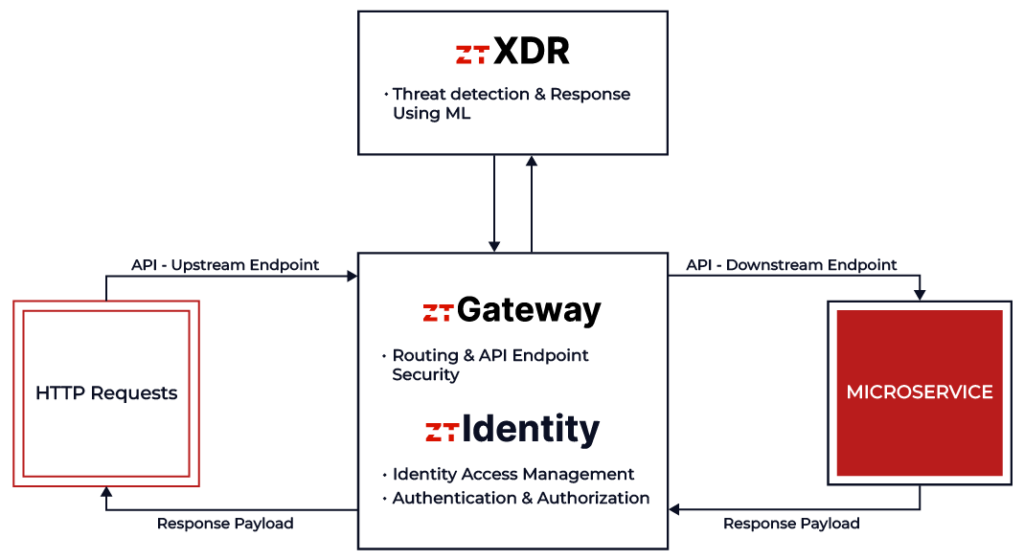
ztPolicyServer is engineered to provide security, identify and respond to threats. Using Machine Learning (ML) algorithms, a robust API Gateway, and an integrated Identity system for Access Control, it proactively mitigates threats before they can breach your defenses. ztPolicyServer can be configured in minutes with just a few clicks.
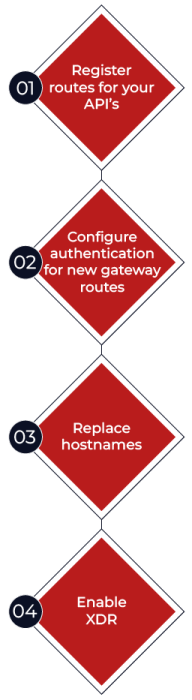

In the ztPolicyServer portal, specify the OpenAPI doc URI to the API that you want to route.
Generate client secret and bearer token. The generated bearer token will be used to protect the API.
Replace hostnames to match the newly configured upstream gateway routes from Step 1.
Enable XDR to capture traffic logs and apply machine learning to identify and response to threats.
At ZeroTrusted.ai, we are committed to providing the highest level of protection for your resources.
Contact us today to learn how our innovative technologies and machine learning can help you achieve true Zero Trust Security.