
ztPolicyServer is a pioneering security solution that melds Intruder Prevention Systems with advanced Machine Learning, a reliable API Gateway, and an Identity for Access Control framework. By proactively detecting and neutralizing threats, it ensures robust digital protection while streamlining policy management and access control. The blend of these technologies within ztPolicyServer not only fortifies your data security but also enhances operational efficiency, making it an indispensable asset for modern digital enterprises.
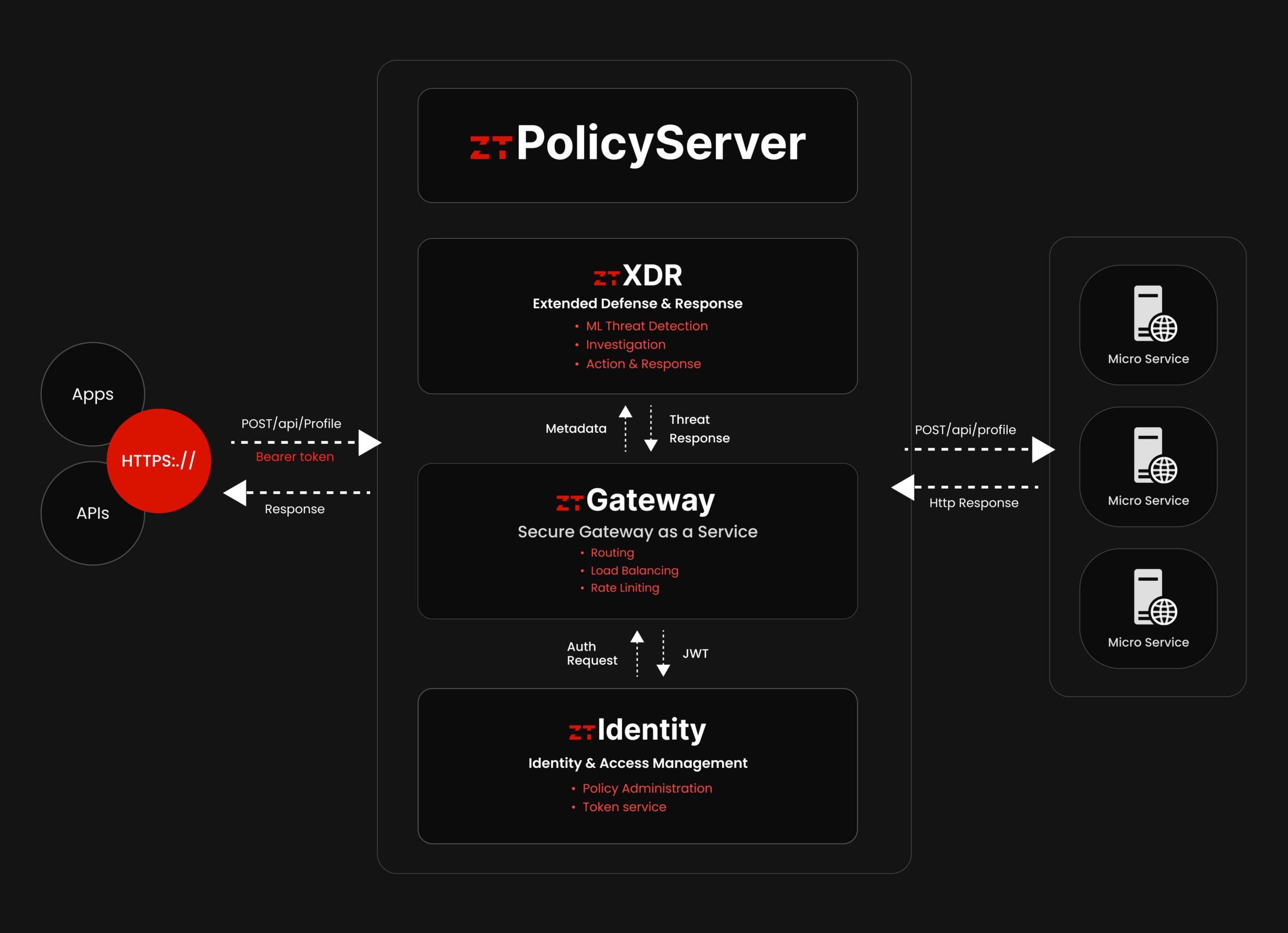
In today’s digital era, safeguarding sensitive data while ensuring seamless access is a paramount concern for businesses. Enter ztPolicyServer, a revolutionary product engineered to epitomize security and access control in a tech-driven business landscape. Our solution seamlessly amalgamates Intruder Prevention Systems (IPS) with cutting-edge Machine Learning (ML) algorithms, a robust API Gateway, and an intuitive Identity for Access Control framework.
ztPolicyServer’s Intruder Prevention facet is vigilant around the clock, proactively identifying and neutralizing threats before they can breach your defenses. With the integration of Machine Learning, our system continually evolves, adapting to new threats and fortifying your digital bastion. The API Gateway orchestrates secure interactions between your applications and external systems, ensuring data integrity and optimized performance. Simultaneously, our Identity for Access Control framework streamlines policy management and access control, fostering a secure yet user-friendly environment.
With ztPolicyServer at the heart of your digital operations, not only will your data remain shielded from unauthorized access, but the automated policy enforcement and real-time threat mitigation will propel your business towards a horizon of minimized risks and maximized operational efficacy. The amalgamation of these tech-savvy features makes ztPolicyServer a vanguard in fostering a robust, secure, and efficient digital ecosystem for your enterprise.

We use machine learning algorithms to identify abnormal or suspicious behavior in network traffic. The process involves collecting HTTP traffic data, extracting relevant features, and training a machine learning model on labeled data to classify incoming traffic in real-time as normal or abnormal. If the model detects an anomaly, the system can trigger a response such as blocking the traffic or alerting security teams. This approach can improve the security posture of an organization, but the accuracy of the system depends on the quality of the training data and the features selected for analysis.
ztXDR applies Machine Learning (ML) to enhance security by leveraging behavorial analysis and threat detection
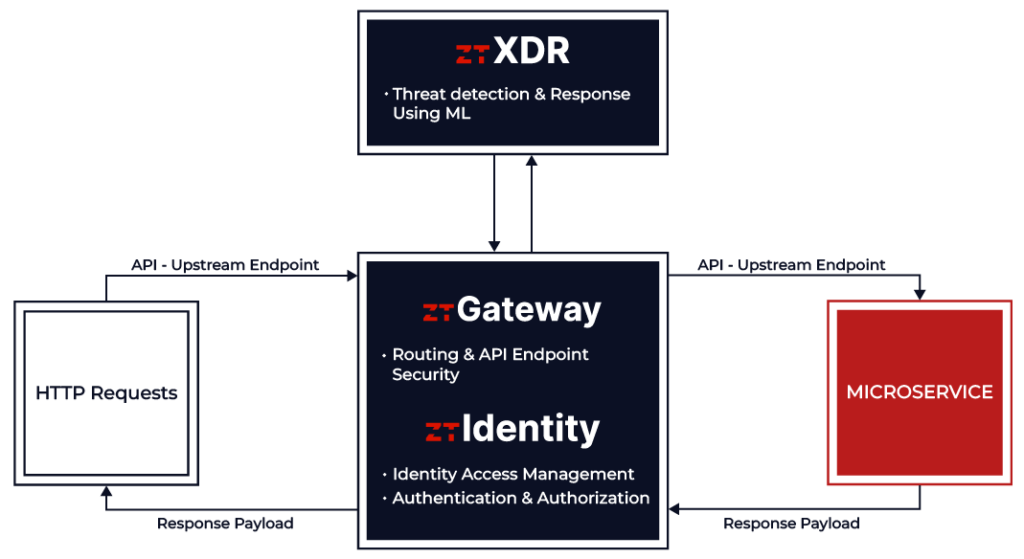
ztGateway provides rapid deployment of microservices apps along with an array of advanced security systems, including integrated Identity Access Management (IAM). These cutting-edge technologies collectively establish a secure access point for authorized applications, safeguarding against unauthorized access and various cyber threats.
ztGateway operates within a secure cloud environment and is designed to integrate effortlessly with your existing infrastructure. By filtering and inspecting all incoming and outgoing traffic for malicious activity, ztGateway ensures optimal security. Our gateway servers are under continuous monitoring and receive regular updates to stay ahead of emerging threats, providing your network with unwavering protection.
ztIdentity helps manage electronic identities through a mix of processes, policies, and technologies, ensuring only authorized individuals access specified resources. Key components include Identity Provisioning, Authentication, Authorization, Single Sign-On, Multi-Factor Authentication, Directory Services, Role-Based Access Control, Audit and Compliance, Federated Identity, Access Management Policies, and Self-Service Capabilities. IAM is crucial for meeting security and compliance requirements, enhancing productivity, and safeguarding against unauthorized access and data breaches.
Web3.Storage is the easiest way to build on the decentralized web from hackathon projects to production code at scale.
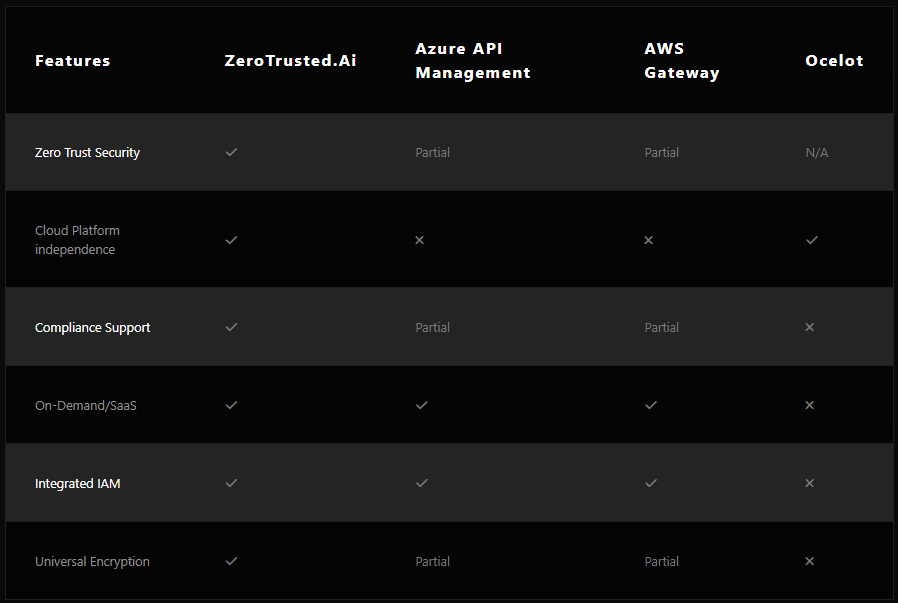
At ZeroTrusted.ai, we are committed to providing the highest level of security for your infrastructure.
Contact us today to learn how our innovative technologies and machine learning can help you achieve true Zero Trust Security.